Article Overview
The following article describes the Resources that can be created using the Integrate tab and the Services screen.
Navigate to the Services Screen
(See Figure 1 and Figure 2)
To navigate to the Services screen, perform the following steps:
Figure 1: Integrate Tab
- Click the Integrate tab.
Result:
The Integrate tab options appear:
Figure 2: Services
- Click the Services option (2).
Result:
The Services screen appears:
Figure 3: Services Screen
- Click the Resources tab (3).
Resources Screen
The Resources screen contains and enables to create (1) the following resources:
- Keys (2)
- Amazon Web Services (AWS) credentials (3)
- File Storage Server (4)
- Database (DB) Server (5)
- Pretty Good Privacy (PGP) Key (6)
- Salesforce (7)
- Payment (8)
- Dataverse (9)
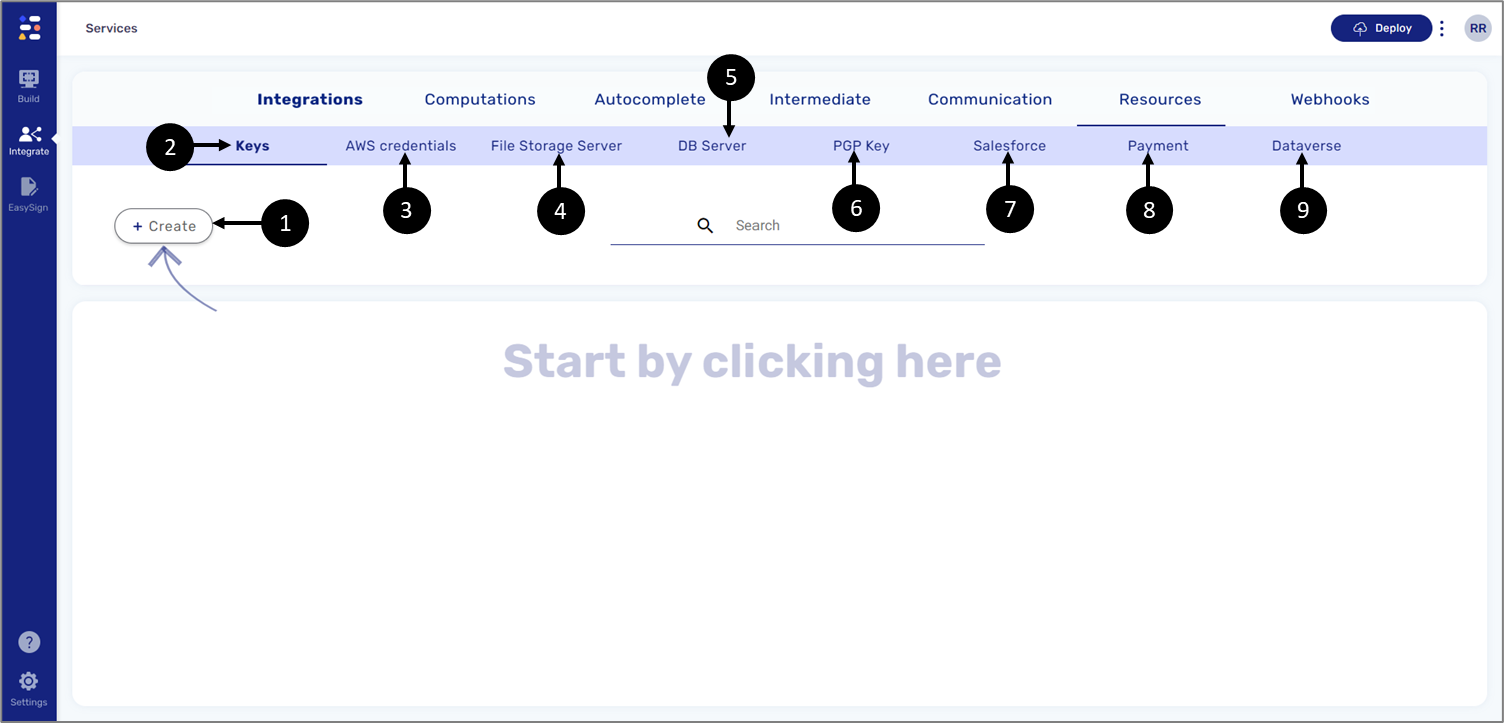
Figure 5: Resources Screen
Keys
(See Figure 6 and Figure 7)
This resource creates a key-based authentication. Using keys is a more secure and encrypted method of authorization that allows an end-user to gain access to target resources with the help of secret keys that are stored and guarded in a secure location by the end user.
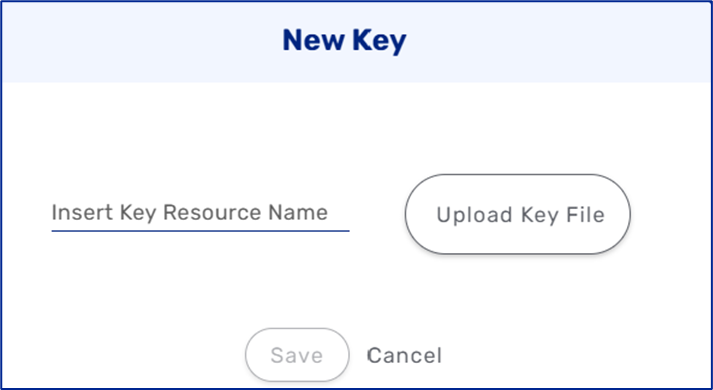
Figure 6: Creating a New Key
After uploading a key file, a dropdown for key type selection appears with the following options:
- Rivest-Shamir-Adleman (RSA) - this type utilizes a public key for encryption and a private key for description.
- Elliptic Curve (EC) - this type is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields.
- Advanced Encryption Standard (AES) - this type is a symmetric block cipher algorithm with a block/chunk size of 128 bits. It converts individual blocks using keys of 128, 192, and 256 bits.
- JSON Web Key - this type uses a JSON data structure that represents a set of public keys.
- x509 Certificate - this type is a digital certificate that uses the widely accepted international X.509 Public Key Infrastructure (PKI) standard to verify that a public key belongs to the user, computer, or service identity contained within the certificate.
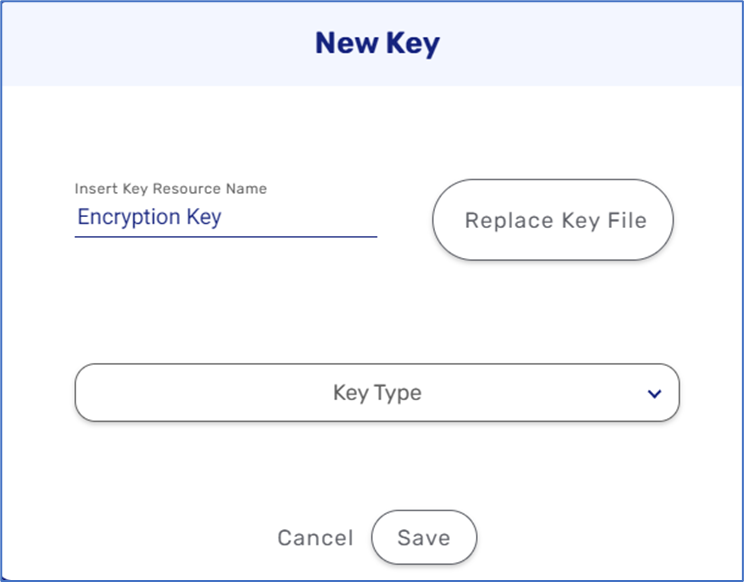
Figure 7: Key Type Dropdown
This resource can used with the following steps:
- Rest API
- File Encode-Decode
AWS Credentials
(See Figure 8)
This resource creates AWS credentials resource. When interacting with AWS, your AWS security credentials are used to verify your identity and whether you have permission to access the resources that you are requesting. AWS uses the security credentials to authenticate and authorize your requests. For example, if you want to download a protected file from an Amazon Simple Storage Service (S3) bucket, your credentials must allow that access. If your credentials are not authorized to download the file, AWS denies your request. This resource can be used when creating a File Storage Server resource.
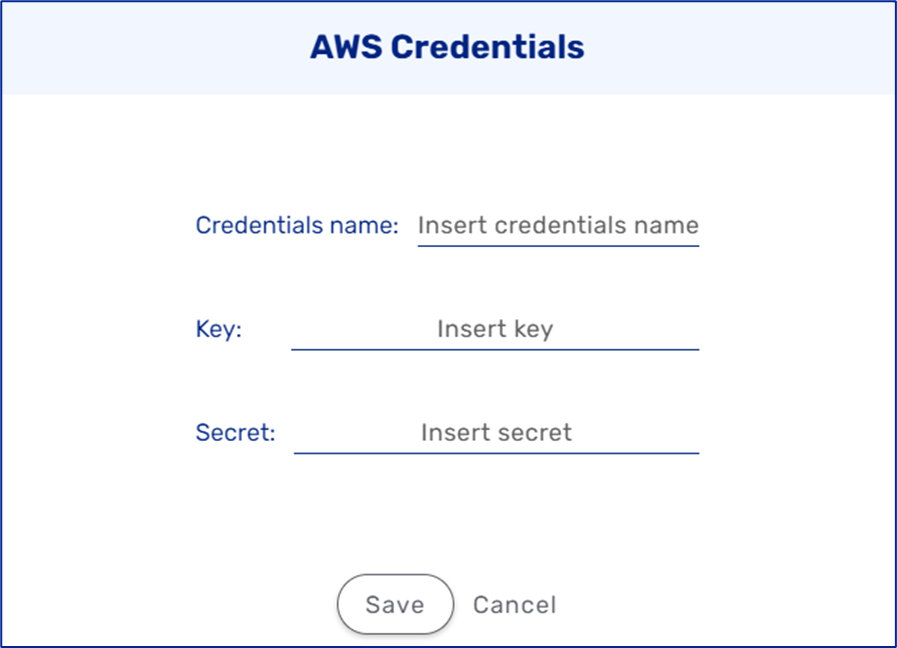
Figure 8: AWS Credentials
File Storage Server
(See Figure 9)
This resource creates a file storage server resource that can be used in the File Storage Service step.
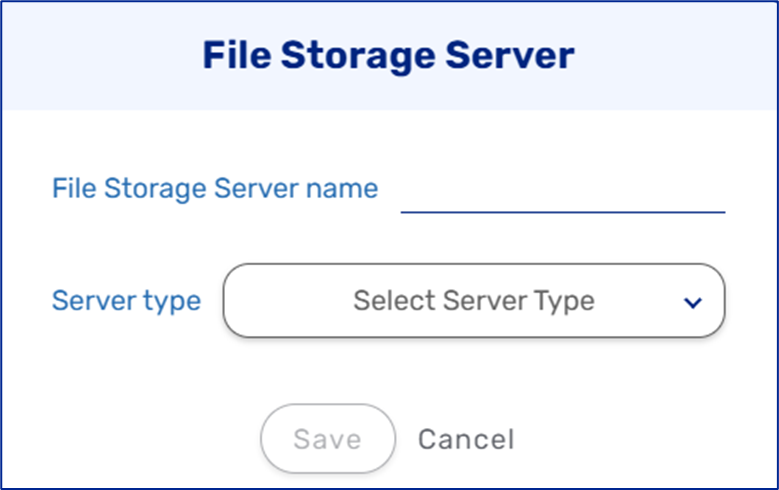
Figure 9: File Storage Server Selection
DB Server
(See Figure 10)
This resource creates a DB server. This type of server uses a database application that provides database services to other computer programs or computers, as defined by the client–server model. Database applications available to select in EasySend are:
- MySQL
- PostgreSQL
- Microsoft SQL
In addition to providing a DB Server Resource Name (1) and selecting a Database Type (2), the following information must be provided:
- Host Name / IP (3)
- Port (4)
- Databases (5)
- Comment (6)
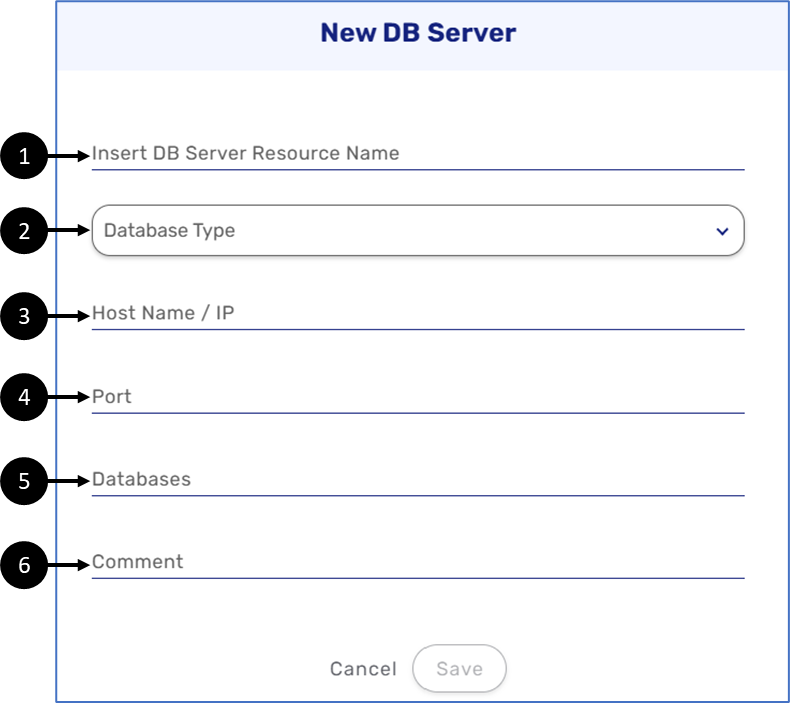
Figure 10: New DB Server
This resource can used with the SQL Query step.
MySQL
(See Figure 11)
MySQL is an open-source relational database management system. A relational database organizes data into one or more data tables in which data may be related to each other, these relations help structure the data. SQL is a language used to create, modify, and extract data from the relational database, as well as control user access to the database. After selecting this type of database it is required to provide a username and password.

Figure 11: DB Server - MySQL
PostgreSQL
(See Figure 12)
PostgreSQL is a free open-source database system that supports both relational (SQL) and non-relational (JSON) queries. It is a back-end DB for dynamic websites and web applications. PostgreSQL supports the most important programming languages. After selecting this type of database it is required to provide a username and password.
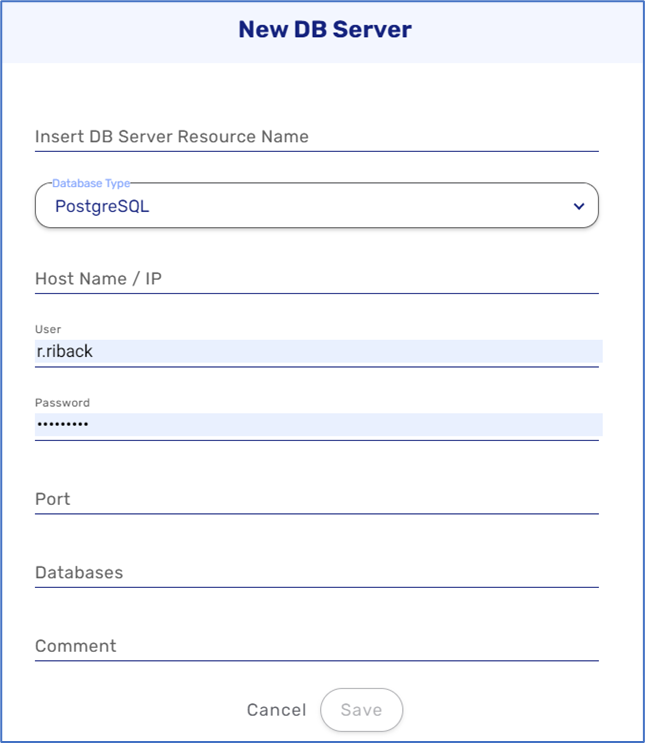
Figure 12: DB Server - PostgreSQL
Microsoft SQL Server
(See Figure 13)
Microsoft SQL Server is a proprietary relational database management system developed by Microsoft. As a database server, it is a software product with the primary function of storing and retrieving data as requested by other software applications - which may run either on the same computer or on another computer across a network. Like other relational database management system software, Microsoft SQL Server is built on top of SQL, a standardized programming language used to manage databases and query the data they contain.
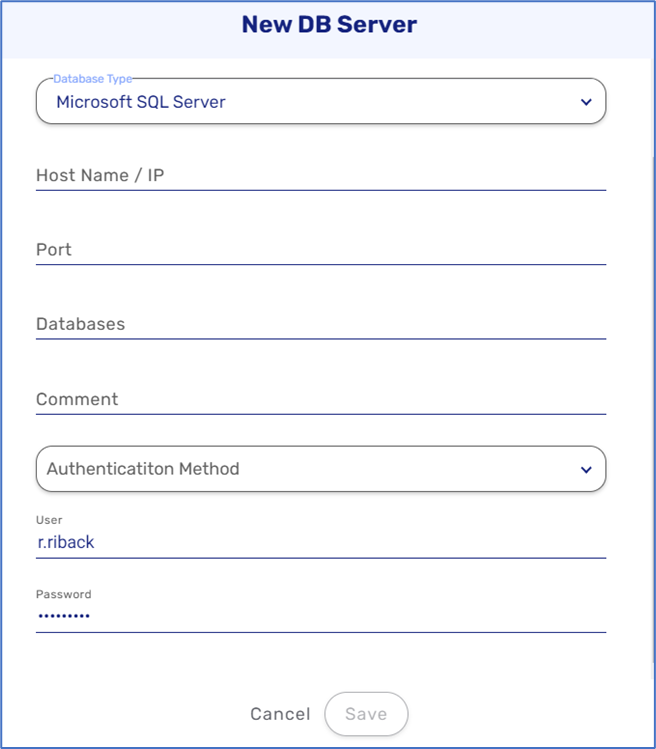
Figure 13: DB Server Type - Microsoft SQL Server
After selecting this type of database it is required to select an Authentication Method:
- Simple User & Password
- Windows Authentication (Windows New Technology LAN Manager (NTLM)) - a suite of security protocols offered by Microsoft to authenticate users’ identity and protect the integrity and confidentiality of their activity. At its core, NTLM is a Single Sign-on (SSO) tool that relies on a challenge-response protocol to confirm the user without requiring them to submit a password.
In addition, it is required to provide a username and password.
PGP Key
(See Figure 14)
This resource creates an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of email communications. This resource can used with the File Encode-Decode step.
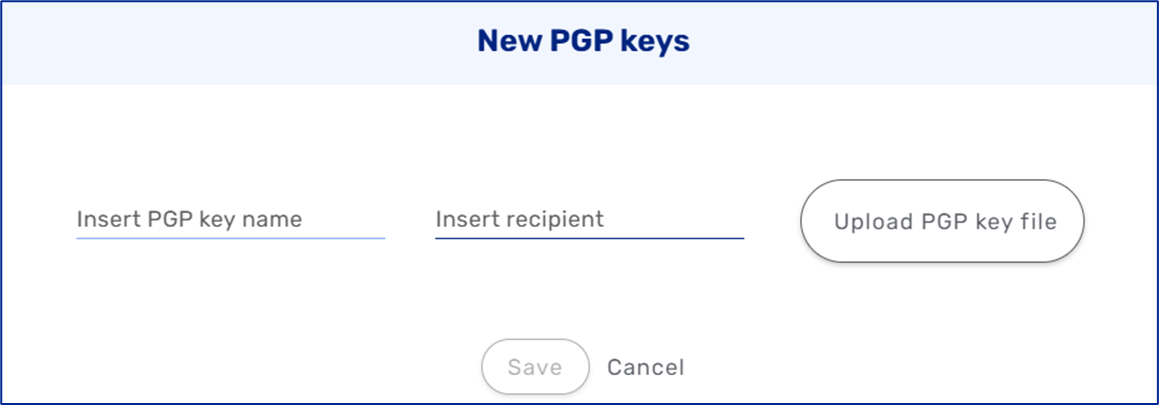
Figure 14: New PGP Keys
Salesforce
Creates a new Salesforce environment. For detailed information about Salesforce two-way integration, see the Salesforce EasySend Two-way Integration article.
Payment
Creates a new payment resource:
- Credit Guard - for additional information, click here.
- Stripe - for additional information, click here.
Dataverse
Creates a new Dataverse environment. For detailed information about Dynamics 365 two-way integration, see the Dynamics 365 EasySend Two-Way Integration article.