Overview
Learn how EasySend customers can secure their web-based applications in various ways by leveraging built-in security features including:
- AATL
- HSM
- SSO
- Email security
- OTP
AATL and HSM
With EasySend's platform, you can allow your clients to digitally sign documents and conduct digital transactions with trust and convenience, due to the Adobe Approved Trusted List (AATL) and Hardware Security Module (HSM) cryptographic keys storage and management appliance.
The Adobe Approved Trusted List (AATL) employs a cluster of globally trusted digital signing certificates and timestamps services that adhere to international legal and regulatory standards. Electronic signatures are automatically recognized as trusted within Adobe Acrobat and Adobe Reader software, ensuring that every digital signature issued on our platform has been authenticated with the approval of globally recognized certificate authorities (CAs) and Trust Service Providers (TSPs).
While AATL assures that the CA issuing digital certificates is trusted by Adobe for digital signatures, HSMs provide a secure environment for storing private keys linked with those certificates, complementing our platform’s solution for reliable digital signatures.
EasySend employs HSMs to protect vulnerable processes like digital signatures and transactions. HSMs are used to store and manage digital keys associated with these processes, as well as execute cryptographic operations on them.
The HSMs dedicated hardware-based environment provides strong security by storing keys and enforcing strict access rules that prevent unauthorized access, tampering, or key extraction.
Our platform leverages the use of HSMs in digitally signed documents to ensure compliance with industry standards and regulatory requirements.
eSignatures generated using the EasySend files platform are legally binding and enforceable. EasySend's e-Signature services are compliant with a number of eSignature laws and regulations, including ESIGN, UETA, eIDAS, APEC, and PRP, which assure legal recognition of electronic signatures and transactions.
SSO-Protected Journey Sender
EasySend’s Journey Sender feature allows our customers’ representatives to initiate and send digital processes links via email or SMS, through a web-based admin application.
EasySend offers users a range of authentication services and seamlessly integrated solutions for a smooth experience. Moreover, our platform provides multiple layers of protection tailored to address your security needs. Protection of both your end user’s and your company’s personal information is ensured by authentication and authorization processes, while using seamless login experience through Single Sign-On (SSO).
To protect the access to the Journey Sender, customers are encouraged to use the Single Sign-On (SSO) setup, that enable them to access the Journey Sender application conveniently, and ensure that users outside of their organization, who do not have access to the user directory of this organization, will not be able to access this section of the platform.
Customer’s end users accessing the fill-in webflow can also be authenticated and protected using SSO. EasySend supports two of the most commonly used SSO protocols:
- Security Assertion Markup Language (SAML).
- OpenID Connect (OIDC).
Email Security
EasySend allows its customers to bring their own email service, but can also utilize 3rd party email providers if needed.
Our selected list of third-party email suppliers adheres to a range of email security standards, including
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM) - allows the verification of the originality of your messages by adding a digital signature to all outgoing messages.
- Domain-based Message Authentication, Reporting, and Conformance (DMARC)
to safeguard our customers against malicious email attacks.
Optimizing our platform to help prevent spoofing, phishing, and spam of our customers’ email, as well as preventing your messages from being marked as spam, we utilize the SPF, which specifies your authorized servers and domains for outgoing email.
DKIM allows the verification of the originality of your messages by adding a digital signature to all outgoing messages.
In case of failed outgoing messages that do not pass either the SPF or DKIM authentication process, DMARC, allows you to tell the receiving servers what to do with these messages. As a standard email authentication method, DMARC allows for tackling spoofing and other attacks while also issuing reports to review potential risks.
Furthermore, the Authenticated Received Chain (ARC) protocol examines the previous authentication status of forwarded messages, thus even if the email passes SPF and DKIM authentication but the forwarded email failed earlier on, it will appear as unauthenticated. EasySend has implemented all of these aforementioned measures to safeguard our clients against harmful communications, email impersonation, and outgoing email falsely being designated as spam by Gmail.
Securing End User's Uploaded Files
The EasySend platform incorporates multiple levels of defense to prevent end users from uploading corrupt files to the digital process. These levels of defense include upload file size limits, file type and mime-type restrictions, and the ability for implementers to integrate third-party virus-scanning APIs:
- Level 1 file size restriction - EasySend’s platform includes two server-side global validations: it limits the size of a single upload to 5MB and limits the cumulative size of uploaded files to 30MB. (Your company might request modifications to the size constraints.)
- Level 2 file type restriction - to prevent security breaches, the EasySend platform restricts certain file types using an approved media-type list. When an end-user attempts to upload a file, the server does a media-type check by comparing it to the approved media-type list on the server side. Executables are not allowed in any case to be uploaded to the EasySend platform. Further restrictions of the allowed media-type of uploaded files can be configured by Builder users.
- Level 3 integration of 3rd party virus-scanning API - a virus-scanning API provided by our customer or by an external cybersecurity platform can be integrated into the EasySend digital process, allowing uploaded files to be scanned before being uploaded to the CRM/API, and detecting any corrupt files that might still pass the size and file type restrictions validations.
APIs and Integration Layer Security
EasySend’s integration layer allows customers to define the specific ways in which collected data will be transferred to the company’s internal systems. To protect this network communication step, the product supports various security methods.
EasySend's platform supports key-based authentication, which provides a secure and encrypted method of authorization for APIs for controlling access to resources and services. End-users are authenticated using unique cryptographic keys or tokens to verify their identity and allow access to resources based on their permissions. The keys are securely stored on the end user's side and transmitted when making API requests. Our key-based authentications approach is straightforward, scalable, and easy to integrate, while also reducing common security threats associated with password-based authentication. Key type selection options include:
- RSA
- EC
- AES
- JSON Web Key
- x509 Certificate
PGP Keys provide cryptographic privacy and authentication for data communication by using a PGP key pair that consists of a freely shared public key for encrypting communication and a secret private key securely kept by the user for decrypting communication. The PGP key can be used for texts, emails, files, directories, and entire disk partitions, increasing the security of communications.
CAPTCHA
To improve the security of our web services by distinguishing between humans and bots, our Builder users can add a CAPTCHA component anywhere along the digital journey.
Using the CAPTCHA feature helps ensure the integrity of user interactions reduce the risk of various automated attacks and automated data extraction, and prevent fraud or abuse by bots or other non-human tools and scripts on EasySend digital processes. Development tools or URL manipulations to bypass the feature are also blocked by the CAPTCHA mechanism since they’re not verified as human action. The functionality of the feature is based on the reCAPTCHA Google service. To carry on with the process on the EasySend platform, the end-user is either required to check a checkbox (“I’m not a robot”) or, in case of any suspicious actions, solve puzzles (such as picture selection) or complete additional tasks.
Data Retention Policies
EasySend significantly restricts users' data storage, and even when it is saved, it is only for a limited period before being erased at the end of the procedure. EasySend's data retention feature enables the use of stored data for analytics and troubleshooting, as well as the configuration of data retention periods across service logs, journey trackers, and tracking reports.
Data Loss Prevention and Recovery
EasySend's Transaction Logs feature offers our platform users an in-depth overview of their transaction status, allowing them to monitor, maintain, investigate, and troubleshoot a variety of issues. Some of the features include using filters or free text to locate specific transactions, investigating their status across multiple services and steps, monitoring failed service executions by accessing error messages or log files, resuming transactions and re-running transactions and services, and tracking webhooks and retries.
- Resume transactions - when a single or multiple transactions are resumed, all actions and steps from the transaction's last RID (Request Identifier, a unique identifier of an EasySend transaction) are Re-Run.
- Re-Run transactions - re-running a transaction involves running all subsequent functions, actions, and services that occur at the end of each step, simulating the end user's actions each time they click submit. Re-Run is only feasible for transactions with at least one completed or failed RID.
- Re-Run services - the EasySend platform allows users to resubmit a single or multiple service, which will rerun all of the service's actions or steps.
One-Time Password
(See Figure 1 to Figure 3)
A One-Time Password (OTP) is a security feature which is used to authenticate an end-user for a single login session or transaction. Since OTP is valid only for a single session, it is less vulnerable to certain cyber attacks compared to a permanent password. OTPs offer convenience, flexibility and enhanced security to our customers, and are the most used method by them to authenticate end-users accessing EasySend/EasySign processes. EasySend’s customers can easily create and assign OTPs via our standardized feature, which includes customizable time limits, delivery methods, and additional settings. OTPs can also be used for two-factor authentication (2FA), adding another layer of security.
On EasySend's platform, our customers may configure OTPs by setting the:
- expiration time for the OTP code (0.5/1/5/10 minutes).
- maximum number of authorized attempts (3/4/5/10).
- suspension time-period in case of failed OTP attempts (10 minutes/30 minutes/1 hour/24 hours). Delivery methods options include email, SMS, or both.
EasySend’s OTP feature supports two main use cases:
- Identify anyone - the end user provides a valid email or phone number and receives a one-time code to proceed with the process.
- Identify someone (known users) - The end user details (email/SMS) are known in advance, and the OTP code will be sent to those known details. The end user is directed either to a flow of entering the code, or utilizing two-factor authentication flow.
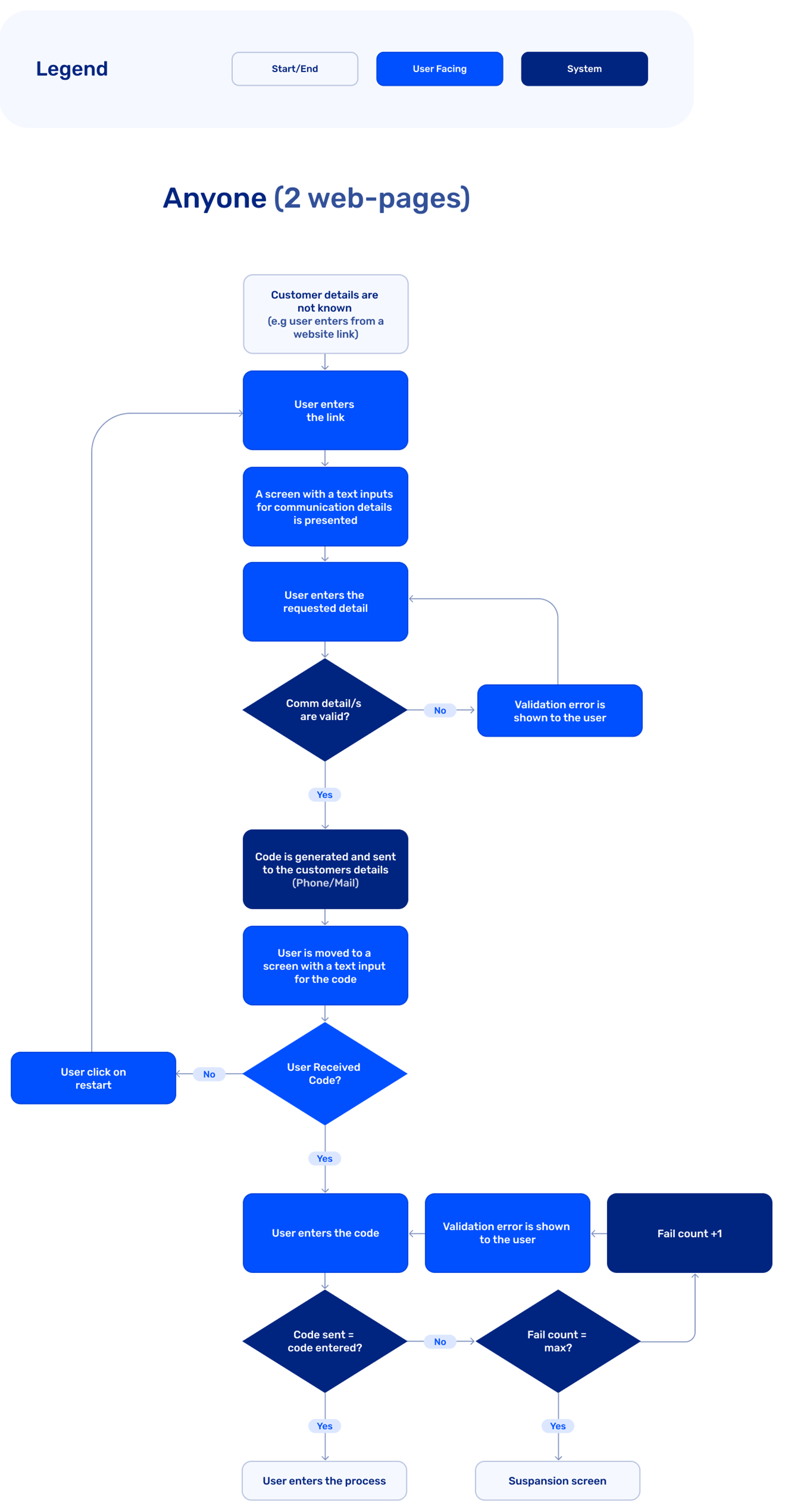
Figure 1: OTP Use Case - Anyone (2 Web-Pages)
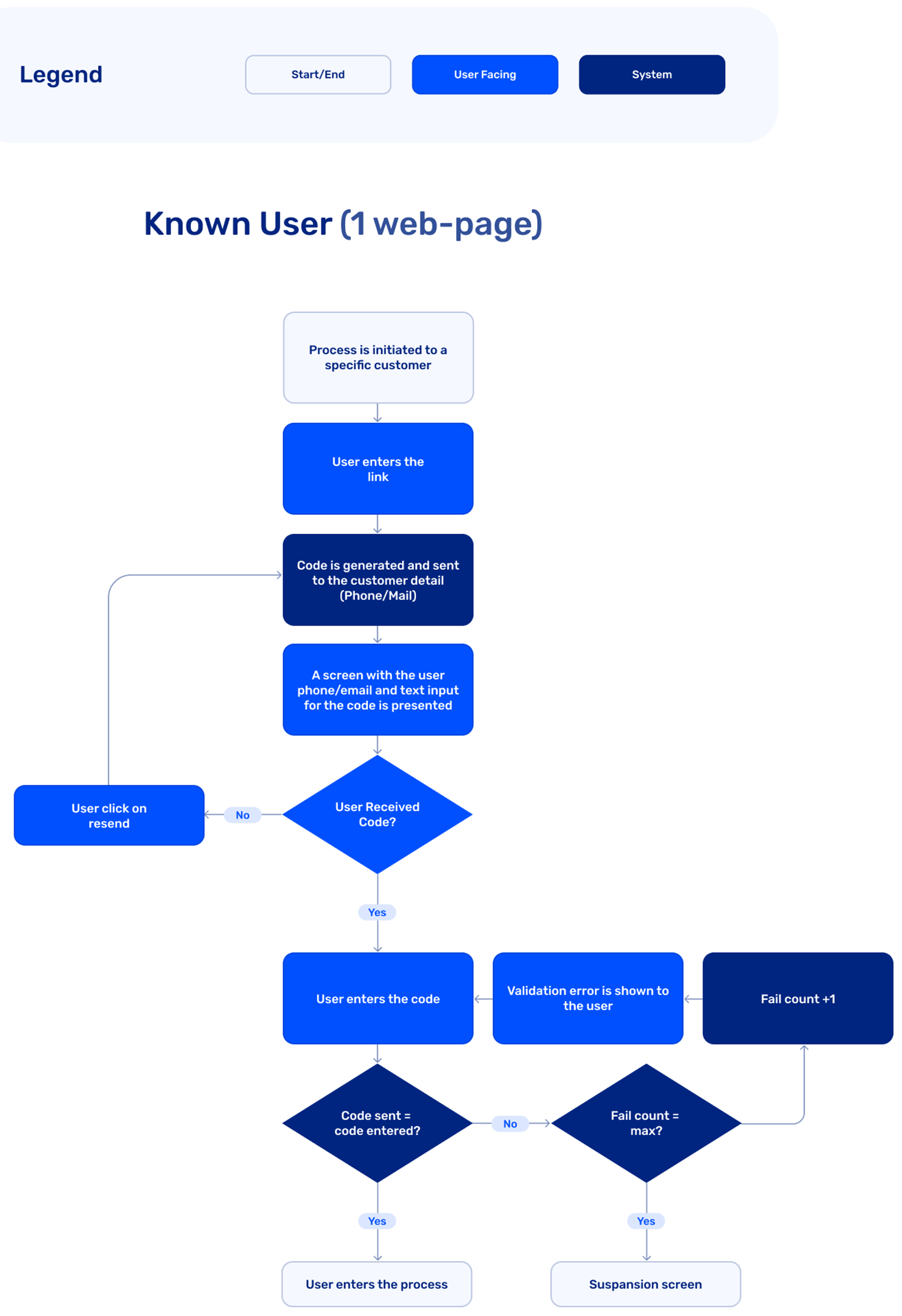
Figure 2: OTP Use Case - Anyone (1 Web-Page)
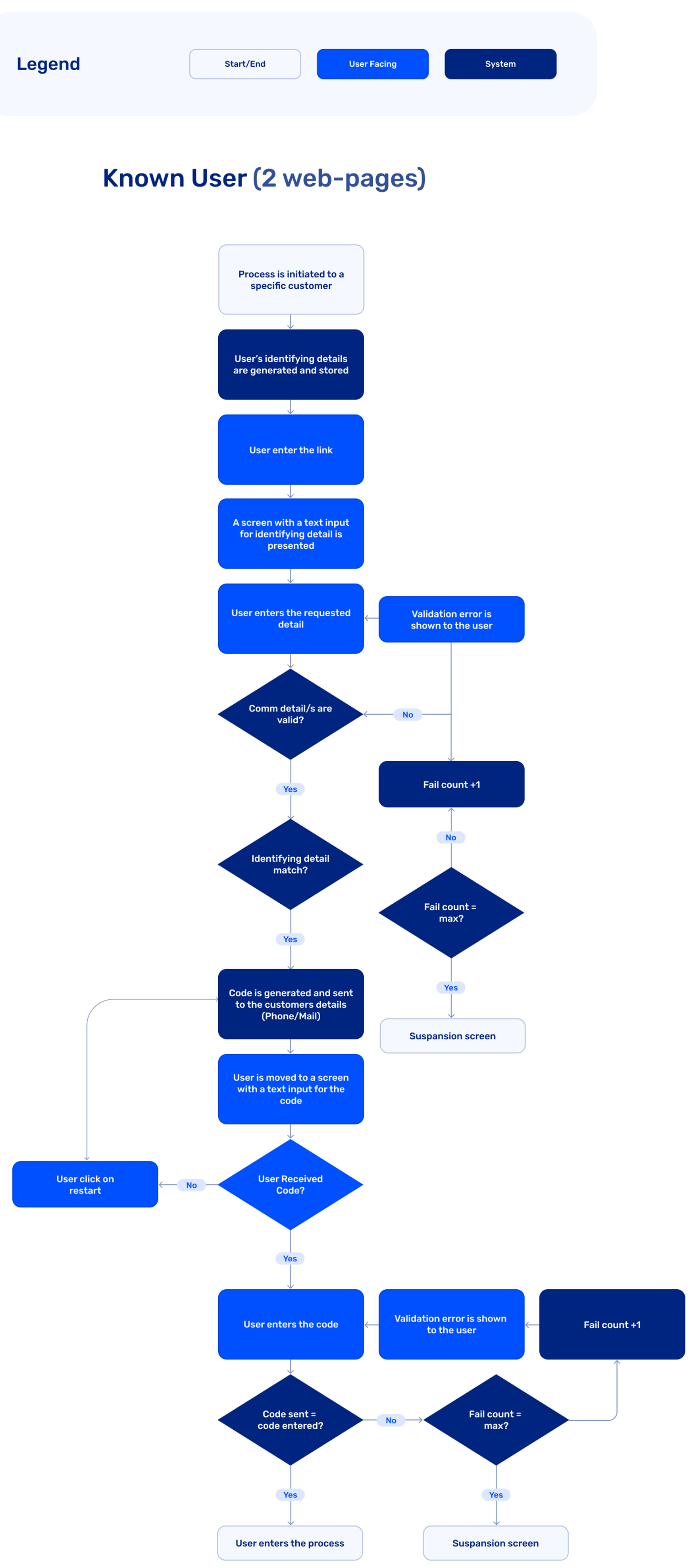
Figure 3: OTP Use Case - Known User (2 Web-Pages)
Add-On Features
(See Table 1)
Table 1 displays EasySend's security offering according to the purchased package.
Table 1: Security Offering
| Security Offering | Baseline | Addon |
Signed PDFs using HSM (AATL) | V | |
Email security - such as DKIM and SPF | V | |
Bring your own email service | V | |
Bring your own SMS provider | V | |
File type validations for uploaded attachments | V | |
Inbound API security | V | |
Integration layer security - REST, SFTP | V | |
OTP | V | |
Google ReCAPTCHA | V | |
Allow different permissions in processes | V | |
Data retention policies | V | |
Data loss prevention & resume from failed | V | |
Streaming of security and audit logs [upcoming] | V | |
SSO for journey sender & user journeys | V |